Wallets, Warnings, and Weak Links
Hello,
It starts with a message. The branding looks credible, the logo checks out too, and the LinkedIn profile shows a few shared connections. The recruiter says they came across your GitHub and want to offer you a contract role with a well-funded AI-meets-DeFi protocol. You skim their site. It’s sleek, believable, jargon-rich in all the expected places. There’s a shortlisting test. It’s sent in a ZIP file.
You unzip it, and the installer launches — a wallet permission prompt flickers on the screen for a second. You click through it without thinking. Nothing happens just yet. The laptop doesn’t freeze. Five minutes later, your Solana wallet is empty.
This is not a random imagination. It’s more or less the flow that blockchain analysis experts have been documenting in hacking campaigns linked to North Korean operators. Fake recruiters, trojan-infected test files and malware are being used to hack wallets.
In today’s piece, I will take you through the evolution of crypto exploits in 2025 and how you could keep yourself safe from some of the most common types of on-chain exploits.
Onto the story now,
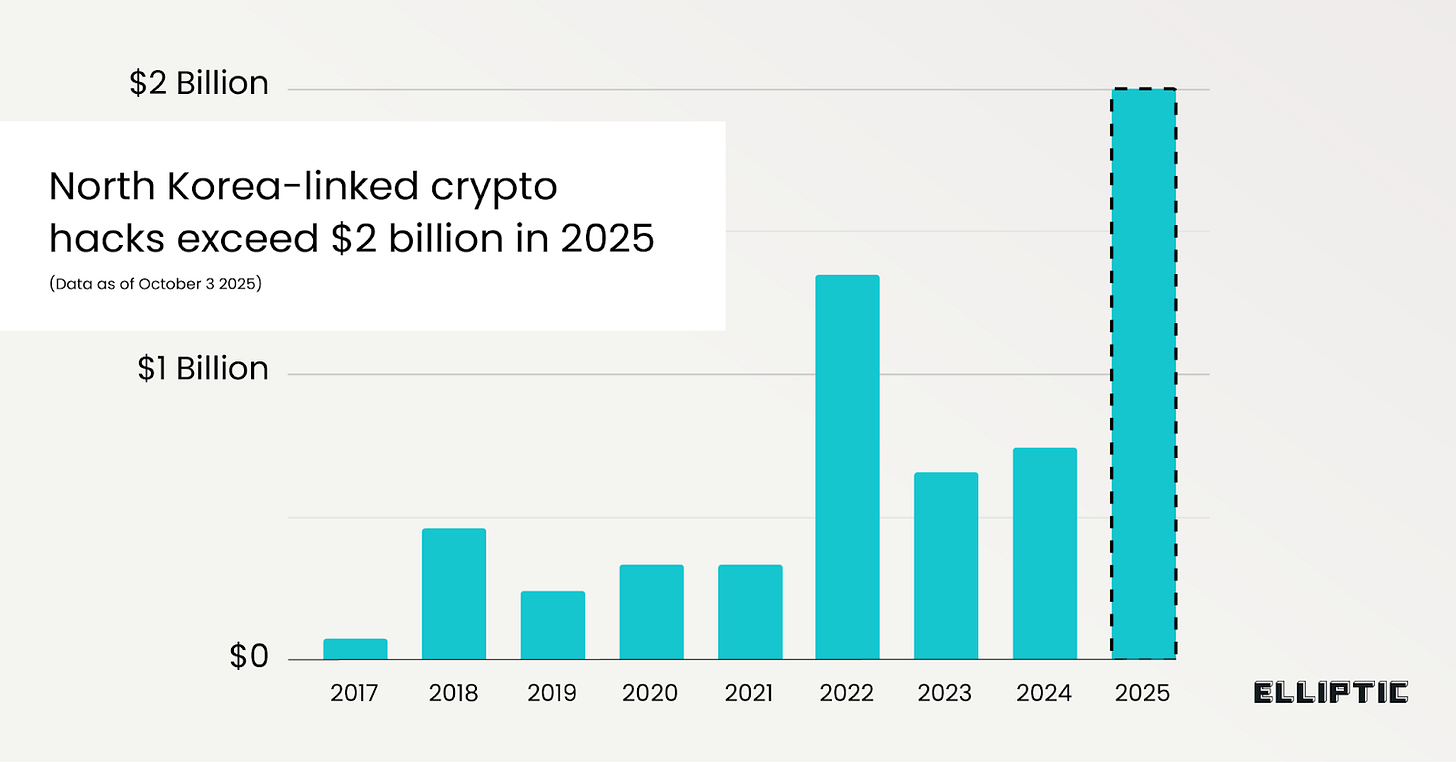
Between January and September 2025, crypto thefts by North Korea-linked hackers crossed $2 billion. According to blockchain analysis firm Elliptic, 2025 is already the worst year on record for digital asset crime by value.
A large portion of the total losses is attributed to the February Bybit hack, which wiped out $1.4 billion from the crypto exchange. The cumulative value of crypto assets stolen by the North Korean regime has now exceeded $6 billion.
Beyond the alarming numbers, what stands out in Elliptic’s report is how the weaknesses in crypto exploits have changed. It notes that “the majority of the hacks in 2025 have been perpetrated through social engineering attacks,” a change from earlier years when North Korea’s record hauls came from breaking infrastructure. Take the infamous Ronin Network hacks in 2022 and 2024, or the DAO hack of 2016.
Lately, that weak link has shifted from infrastructure to human. Chainalysis also reported private key compromises accounting for the largest share (43.8%) of stolen crypto in 2024.
It’s clear that as crypto evolves and security strengthens at the protocol and blockchain levels, attackers are instead finding it easier to target humans holding the private keys.
It is also becoming more organised at this level, rather than random individual targeting. Recent FBI and CISA advisories and news reports described North Korean-linked campaigns that blend fake job offers to crypto engineers, trojanised wallet software, and malicious open-source code contributions to pull off exploits. Although the tools the hackers rely on are technical, the entry point is human and psychological.
The Bybit hack, the largest crypto heist, shows how that plays out at scale. When roughly $1.4 billion of ETH was drained from a wallet cluster, early technical breakdowns pointed to a lapse in signers verifying what they were approving. The Ethereum network did its job correctly by executing valid and signed transactions, but what failed was the manual, human element.
Read: The Bybit Hack
Similarly, during the Atomic Wallet hack, about $35-100 million worth of crypto assets vanished due to malware targeting how private keys were stored on users’ machines.
You see the same idea playing out in many cases. When humans make transfers without verifying the entire wallet address or store keys with minimal security, there’s little the protocol can do to help.
Self-Custody Isn’t Foolproof
“Not your keys, not your coins” still holds, but the problem arises when people stop thinking after that.
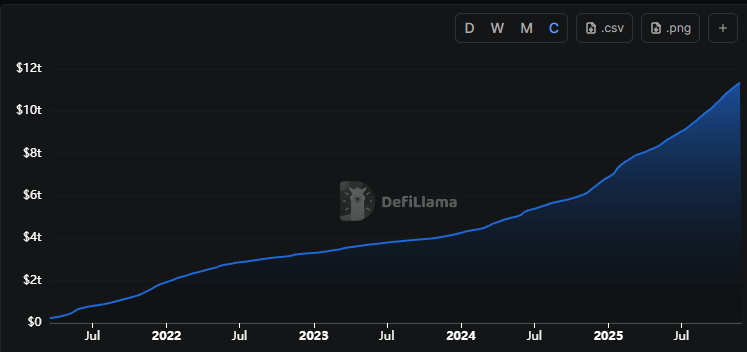
Over the past three years, many users have moved funds off exchanges, driven as much by fear of another FTX-style collapse as by ideological conviction. The cumulative trading volume on DEXs has more than tripled, from $3.2 trillion to $11.4 trillion, over the past three years.
Although it looks like an upgrade in security culture, the risk has moved from custodial to do-it-yourself chaos. Browser extensions on laptops, seed phrases saved in mobile phone chats or email drafts and private keys sitting in unencrypted note apps do little to ward off the danger lurking.
What self-custody was meant to solve was dependency: on exchanges, on custodians, on anyone who could pause withdrawals or go bust. What it has not yet solved is literacy. Private keys give you control, but they also give you full-fledged responsibility.
How do you really address this issue, then?
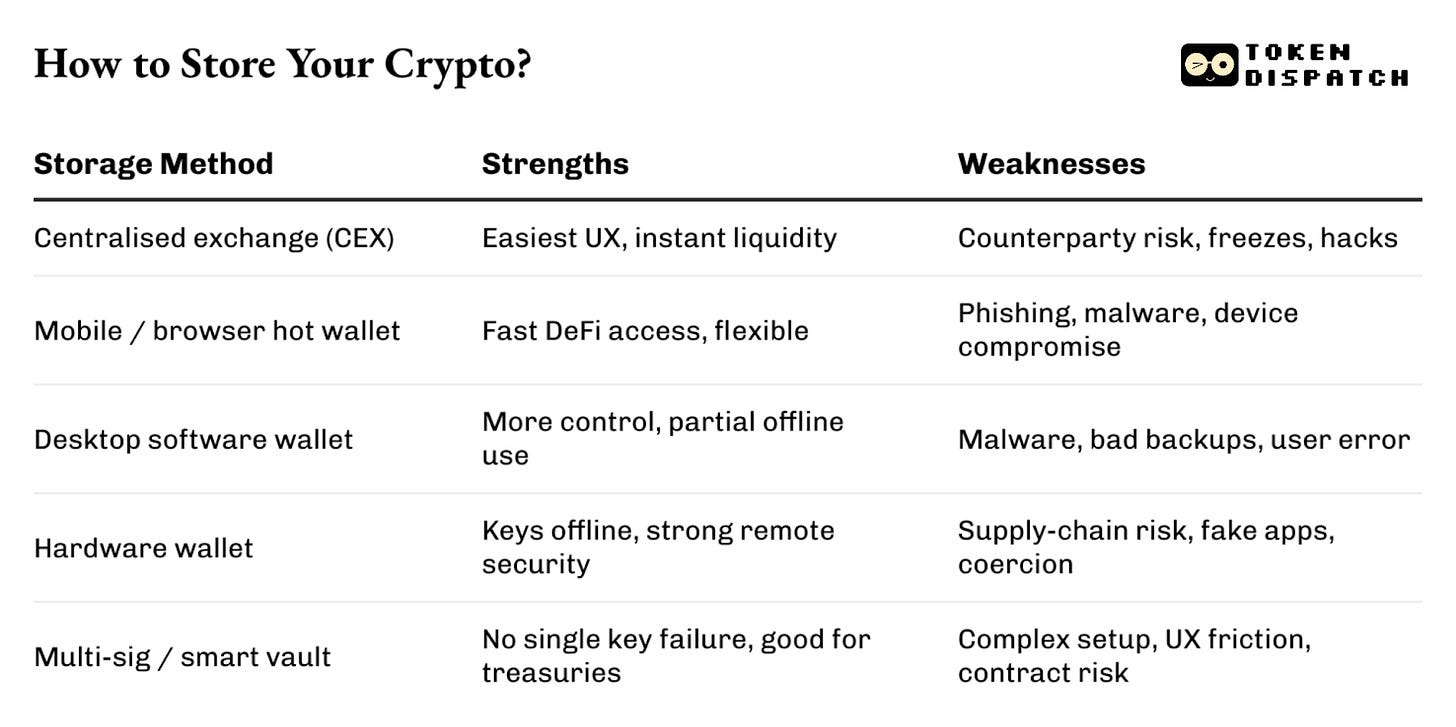
Hardware Wallets Help with Friction
Cold storage fixes part of the issue. It moves your assets offline and puts them in an equivalent of a vault.
Is the problem solved? Partially.
By moving keys off general-purpose devices, hardware wallets can eliminate the need for browser extensions or for approving transactions with a single click. They introduce physical confirmation, a type of friction that protects you.
Not Your Keys? Not Your Coins. Not at This Price Either!
Exchanges get hacked. Hot wallets get drained. Hardware wallets are the only way to truly own your assets.
Meet OneKey: The industry’s leading open-source hardware wallet. It is the easiest, most secure way to take your coins offline and out of reach.
Black Friday is the best time to secure your bag!

We recommend OneKey, no compromises.
Still deciding? Shall we spoil you with some exclusive goodies?
From Nov 28-Dec 2, use code BF25:
- 25% OFF Bundles (Best Value)
- 15% OFF Single Wallets
- Wild Bonus: 2 random buyers get their entire order FREE
It’s the cheapest insurance policy you’ll ever buy for your portfolio
But a hardware wallet is still a tool.
Security teams at wallet providers have been blunt about this. Ledger has reported repeated phishing campaigns piggybacking on its brand with fake browser extensions and cloned versions of Ledger Live. The interface is familiar enough to feel safe, but at some point, the user is prompted to enter a recovery phrase. Once the phrase is compromised, the rest is a foregone conclusion.
People can also be duped into entering recovery phrases on fake firmware update pages.
What a hardware wallet does is shift the attack surface and introduce friction points to reduce the likelihood of an exploit. It does not entirely remove it.
Separation is Key
Hardware wallets work best when the user buys them from trusted channels and secures the recovery material offline and out of sight.
Most people who live in this stuff every day, including incident responders, on-chain sleuths, and wallet engineers, advise separating and diversifying risk.
One wallet for day-to-day use, another that rarely, if ever, touches the internet. Small balances for experimentation and DeFi farming, while keeping the larger ones vaulted, which require multiple steps to access.
On top of all this sits basic hygiene.
Some boring, repeated habits can often save the day. Never type a seed phrase into a website, no matter how urgent the pop-up sounds. Check the full address on the hardware screen after a copy-paste. Pause before approving any transaction that isn’t clearly under your control. Be sceptical of unsolicited links and “support” messages until proven otherwise.
None of these behaviours guarantees safety. There is always some residual risk. But each of these takes a step further in reducing the risk.
Right now, the biggest threat to most users isn’t a zero-day exploit. It’s the message they didn’t double-check, the installer they instantly downloaded and ran because the job offer sounded good, and the seed phrase they wrote on the same piece of paper as their grocery checklist.
When people in charge of billions treat these risks as background noise, they end up as case studies with “exploits” labelled across them.
That’s it for today. I’ll see you with the next one.
Until then … stay sharp,
Disclaimer:
- This article is reprinted from [thetokendispatch]. All copyrights belong to the original author [Prathik Desai]. If there are objections to this reprint, please contact the Gate Learn team, and they will handle it promptly.
- Liability Disclaimer: The views and opinions expressed in this article are solely those of the author and do not constitute any investment advice.
- Translations of the article into other languages are done by the Gate Learn team. Unless mentioned, copying, distributing, or plagiarizing the translated articles is prohibited.
Related Articles

How to Do Your Own Research (DYOR)?

What Is Fundamental Analysis?

What Is Ethereum 2.0? Understanding The Merge

What Is a Cold Wallet?

What is GateToken (GT)?